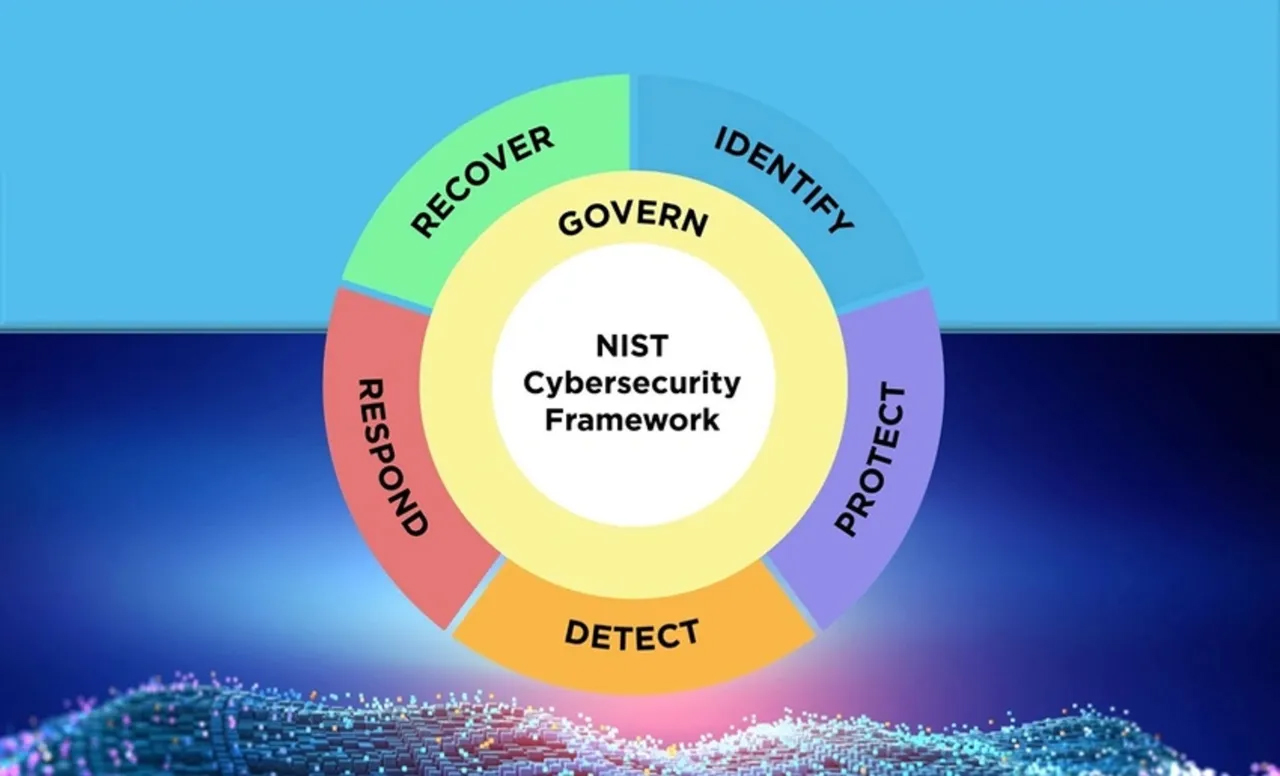
One of a vCISO’s first tasks should be to pick or affirm an industry cybersecurity framework to use for building and evaluating a cybersecurity program. The NIST Cybersecurity Framework should be considered – but it is too high level to effectively audit and implement without further guidance. The National Institute of Standards and Technology (NIST) has multiple frameworks available for security and risk management (NIST, 2024). Johnson in Chapter 4 of his book points out that the primary difference between standards and frameworks is the specificity of standards versus frameworks (Johnson et al., 2024 Chapter 4). More precisely – the text indicates that a standard outlines a “a specific way of achieving a control objective”. The NIST Cybersecurity Framework 2.0 (CSF) and NIST 800-53 (800-53) standard/compliance frameworks are illustrative of this difference between frameworks and standards. Note that 800-53 is generally considered “both” – but I am going to focus on the standard aspects.
Authentication is the concept of verifying that someone is who they say they are when logging into a system. The CSF is divided into top level functions (Task Force, 2024):
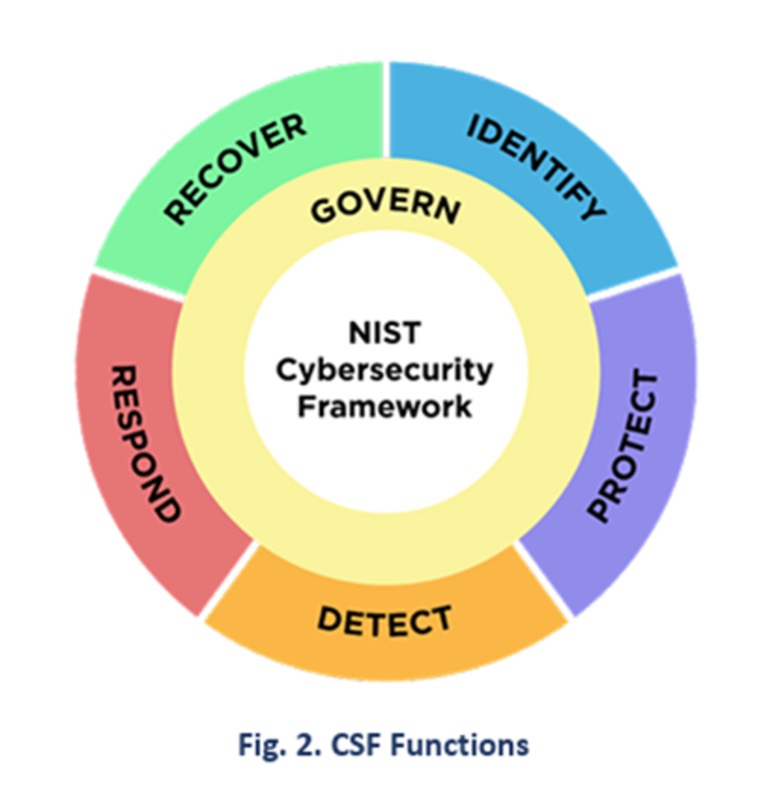
Each function is then broken down into categories and further into sub-categories. The Protect function has 5 categories:
- Identity Management, Authentication, and Access Control (AA)
- Awareness and Training (AT)
- Data Security (DS)
- Platform Security (PS)
- Technology Infrastructure Resilience (IR)
The final breakdowns of each category (the lowest level) are subcategories, and under Protect (PR) Identity Management, Authentication, and Access Control (PR.AA) there are 6 subcategories:
PR.AA-01: Identities and credentials for authorized users, services, and hardware are managed by the organization
PR.AA-02: Identities are proofed and bound to credentials based on the context of interactions
PR.AA-03: Users, services, and hardware are authenticated
PR.AA-04: Identity assertions are protected, conveyed, and verified
R.AA-05: Access permissions, entitlements, and authorizations are defined in a policy, managed, enforced, and reviewed, and incorporate the principles of least privilege and separation of duties
PR.AA-06: Physical access to assets is managed, monitored, and enforced commensurate with risk
This is the lowest level of detail that the CSF framework goes – and I would equate this to Policy level documents with a company or organization. If an organization was required to be compliant with the CSF – then they would create a policy document for authentication that includes the 6 subcategories above as policy requirements. This level of detail does NOT help an IT implement specific rules or tools – but it gives them the trade space to make those decisions.
800-53, on the other hand, is very detailed around authentication (Task Force, 2020). In fact – a quick search of “authentication” in the document lists 259 instances. There is an entire “family” of controls around identification and authentication. I am showing some of the controls here (not all):
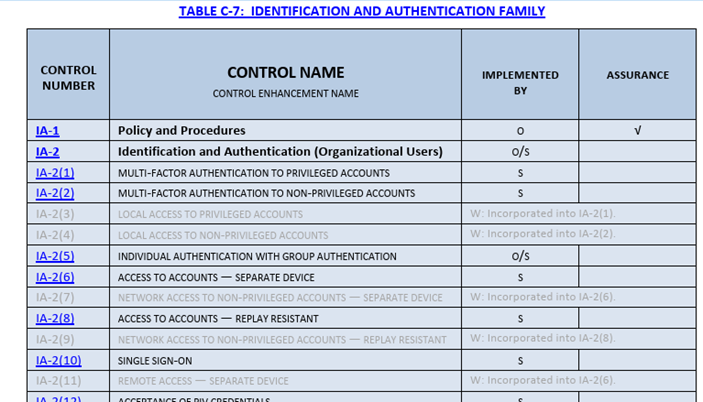
Picking one, IA-2(1) as an example – here is the detail provided:
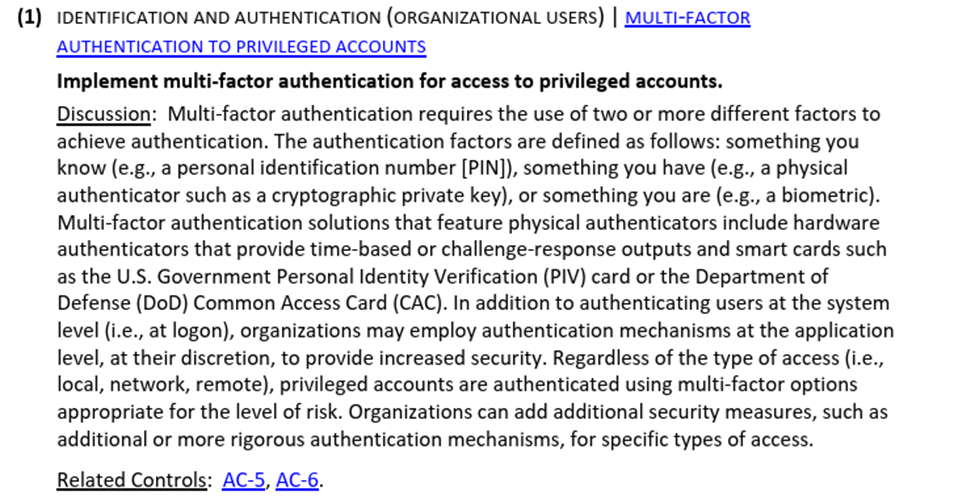
This level of detail gets MUCH closer to helping an IT team implement it – standards level. Basically – these are lower-level requirements than in the CSF (framework level) and they are not quite the operating procedure level – they are certainly more detailed than the framework level found in the CSF. The final level of procedures would likely contain a detailed implementation plan for a specific control by a specific vendor – something that is very easily auditable. Even so – the 800-53 control detail is probably auditable as well.
Your Rhindon Cyber vCISO will help you sort through frameworks/policies/standards and procedures and give you confidence in your cyber resilience.
Johnson, R., Weiss, M., & Solomon, M. (2024). Auditing it infrastructures for compliance. Jones & Bartlett Learning.
NIST. (2024, September 25). Frameworks. https://www.nist.gov/frameworksLinks to an external site.
Task Force, J. (2020). Security and Privacy Controls for Information Systems and organizations. U.S. Dept. of Commerce, National Institute of Standards and Technology.
Task Force, J. (2024). The NIST Cybersecurity Framework (CSF) 2.0. U.S. Dept. of Commerce, National Institute of Standards and Technology.
Rhindon Cyber offers vCISO services securing financial service firms, high net worth individuals, Catholic non-profits and the small and medium business market. We are craftsman focused on providing cyber resilience for people so that they can focus on becoming what God intended.
David Mosher is a CEO, Board Member, virtual Chief Information Security Officer (vCISO), MS in Cybersecurity, PhD Student in Cybersecurity Mgmt.